August 30, 2017
When Fines Are Not Enough: Data Risk Calls for Data Monitors
Data is the lifeblood of any modern organisation – it controls how we operate, how we make money and assists with driving competitive advantage within any industry. Even for the most traditional brick and mortar organisations, data is crucial in all forms: from intellectual property (IP) to a company’s most basic customer lists and staff records.
The Crossroads of Organisational Risk
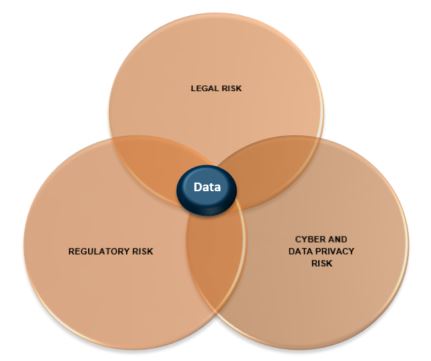
Legal, privacy, and regulatory organisational risk all overlap around data. Financial institutions face severe fines if bank transactions (all stored electronically) are not monitored continuously and tested independently. Retail organisations must properly manage customer information daily or suffer reputational risk. Data is a slippery beast to control as it is highly portable and malleable and therefore can easily escape into different places and take different forms. Consider a customer list being downloaded from a secure CRM system into Excel and later being copied to an unencrypted USB drive so that an employee can work from home. In situations like these, data can easily slip out of the control of the organisation responsible for its safeguarding.
The vast implications of data risk often include very personal and private information. Although not the case with all forms of IP (i.e. designs and copyright), it is true for much of the data that organisations hold. Any list of stakeholders must also include the individuals who are referenced in the data itself, especially given the personal consequences they face if the data is mismanaged. Inevitably the data risks faced by an organisation, including its’ customers and employees, will result in immediate brand dilution affecting the bottom line. Organisations that have been harmed by these breaches have lost recurring and future customers – signalling a trend that is here to stay.
Data warrants additional protection due to the increased number of stakeholders, especially as those stakeholders have limited power, control or influence over how their data is handled or managed once within the organisation. In many instances, the only action that customers can take is to move their business to an alternative provider, assuming one is available. Even at a new organisation, there is no guarantee that the data is more secure than within the hands of the previous organisation.
What is more concerning is that the potential harm facing the individuals whose data is subject to loss has a potentially long life – once the data is compromised, it is nearly impossible to stop or reverse the damage. Not only can it have long-lasting financial implications, but it can also have reputational and indirect costs to the individuals impacted. A reduction in credit status and continual fights to gain control of their own identity are a few examples among the many costs to customers.
Regulatory Reach is Limited - Fines Alone are Falling Short
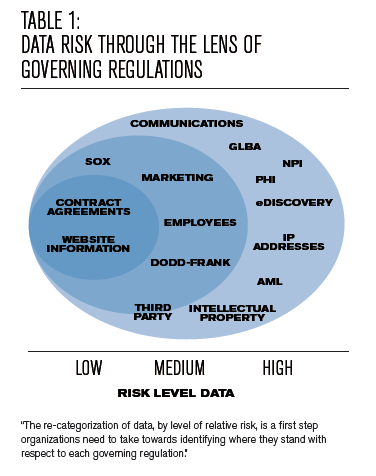
Compounding this already significant risk is the lack of power that regulators have with respect to data. Prior to May 2018, when the EU General Data Protection Regulation (GDPR) becomes effective and with some US states still not mandating comprehensive data breach notification regulations, the reach of the few regulators that exist in this data space is limited (see Table 1). In Europe, GDPR will not entirely solve the problem. Admittedly, it is a large step forward as it brings in both mandatory data breach notification processes and introduces the potential of very large fines (up to 4% of global annual turnover or €20 million whichever is greater). However, even the threat of fines is starting to be diluted. For example, in a blog post by Elizabeth Denham, the U.K. Information Commissioner stated: “It’s scaremongering to suggest that we’ll be making early examples of organisations for minor infringements or that maximum fines will become the norm.” She further dismissed predictions that huge fines would be scaled up to the level allowed under the GDPR compared to previous penalties levied by the Information Commissioner’s Office as "nonsense."
This lack of power is especially evident when compared to the laws and regulations that govern other corporate misdemeanours such as fraud, corruption and bribery, where governments and agencies have large teams focused on these risks and the issuance of fines is ever-increasing. In addition, many regulators have the ability to install independent monitors into an organisation that requires it to remediate weaknesses and ensure that good corporate behaviour is maintained. Organisations often agree to a monitor in the process of a settlement or negotiation with the regulator.
What is worrying is that the regulatory emphasis in respect to data seems to be on fines alone, assuming that this in itself will drive good behaviour. But do fines alone have that desired effect? A sceptical response would focus on the issue of timing and who assumes the fault. If you consider a data breach to be the result of potentially poor controls and management of data – although it should be remembered that no system can be 100% secure – then the focus should be on regulatory activity to drive good controls and management. Fines alone punish the current management and stakeholders financially. There are often large indirect costs companies can incur which should not be forgotten, but they do not necessarily enforce the good behaviour the public and regulators are demanding. It seems to be easier to blame former management, to point the finger elsewhere and to attribute the problem to historic systems; thus, giving the impression that all has been resolved.
Data Monitors
The introduction of independent data risk monitors, similar to those required by regulators following corruption or bribery events, could be one of several approaches to be evaluated as a way forward. A data risk monitor can add visibility and controls and can mitigate future risks by applying technical knowledge to the lifecycle of any and all data in an organisation. End-to-end data insight on the creation, storage, identification, classification, access and security, archiving and destruction stages is imperative to clearly identify potential pitfalls.
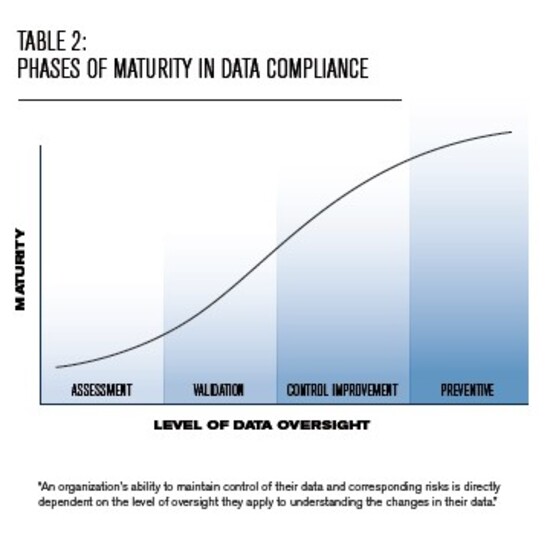
Maturity in data compliance (see Table 2) requires an organisation and the independent data monitor to clearly understand a company’s data lifecycle. The monitor’s technical understanding and ability to validate the company’s regulatory and legal obligations through detailed sampling, data integrity checks, lineage mapping and logic reviews and data validation of unstructured and structured data is critical in order to gauge compliance and related risks.
Integrated Data Governance Program
Today, organisations are addressing data risk disparately. Most often, the budget for the CISO office, which is charged with protecting all data, is often independent and duplicative of the budget for the Legal office, which oversees implementation of information governance solutions. Beyond the obvious overhead inefficiency, this disorganised view of data is harmful and poses great risk to all organisations.
All organisations, therefore, should implement an integrated and effective Data Governance Program that is measured, independently tested and prioritized.
Key Principles of a Data Governance Program:
1. Transparency – Classify data by type(s) of risk posed and keep records of what, where and how data is stored
2. Validation – Confirm consistent reliance on relevant and accurate data
3. Controls – Improve and enhance controls to proactively reduce data risk
A mature Data Governance Program will ensure good information management practices are implemented and will validate that data is dealt with in a well-controlled manner. This drives a number of compelling advantages for an organisation, including:
(a) Data breaches are effectively and efficiently resolved, with the root cause of the breach confirmed so that compromised parties can have confidence in the investigation process.
(b) Validation that any control weaknesses and mishandling of data would be rectified to avoid repeat issues from occurring. This would involve a complete data audit to ensure that processes and controls effectively safeguard the data.
(c) Provision of additional reassurance to individuals impacted by any breach and to any existing or new customers of the organisation that their data was being managed securely.
(d) Protection of stakeholders of the organisation when looking at how the organisation’s business continues to operate and deal with data.
Conclusion
While the expectation is that well-controlled companies should already have Data Governance Programs in place, it is a practice that has not been prioritized by organisations universally. As the data ecosystem continues to increase in pace and size, so will the risks associated with data. As regulators continue to recognize the risk data poses, fines for non-compliance will also increase. But fines alone are not enough to ensure good behaviour. The introduction of independent data monitors will ensure that data is dealt with in the manner that it deserves given its value to the company, stakeholders and the individuals involved.
[1] Denham, Elizabeth. “GDPR – sorting the fact from the fiction”