DOJ Bulk Sensitive Data Rule: Assessing Applicability and Impact to Your Organization
On April 8, 2025, the U.S. Department of Justice’s (DOJ) final rule on Preventing Access to U.S. Sensitive Personal Data and Government-Related Data by Countries of Concern or Covered Persons (the Rule) will take effect. Companies that collect data of a type and volume covered by the Rule will find themselves subject to a level of data security expectation historically reserved for sensitive transactions or companies within the traditional U.S. defense industrial base. The breadth of covered data, the potential complexity of demonstrating compliance if subjected to DOJ inquiry, and enforcement penalties up to and including criminal liability should compel the market to stand up, take notice and get out in front of this new data security regime.[1] This article is intended to be an operational roadmap for how to assess whether the Rule applies to your company and what you should be thinking about if it does.
- What is the U.S. Government Driving At?
Companies that understand why the U.S. government is taking action are more likely to implement a compliance approach responsive to the U.S. government’s equities and thereby mitigate risk.
Put simply, the confluence of new technologies — particularly large language models and AI technologies — that allow for rapid ingestion, processing and inferencing of large data sets presents an emergent and significant threat to U.S. national security. The threat can manifest in threats of various stripes, including facilitating espionage, blackmail and civil unrest through targeted misinformation and disinformation campaigns.
The emergent threat also must be understood in the context of a shifting geopolitical landscape, now marked by major-power competition. In this new world where national security is economic security, policymakers’ thinking as to the balance between economic and national security interests has shifted. National security interests are increasing in prominence and coming to the fore.
- What Does the Rule Do?
There have been many excellent and detailed published summaries of the Rule. Staying at a high level, there are two animating factors of the Rule: (i) control of bulk sensitive data or government-related data and (ii) covered transactions with countries of concern or covered persons. The Rule identifies several sensitive data categories — including human genomic and other ‘omic, biometric, geolocation, and health, financial and personal identifying information. The Rule is triggered when the volume of sensitive data exceeds designated thresholds.
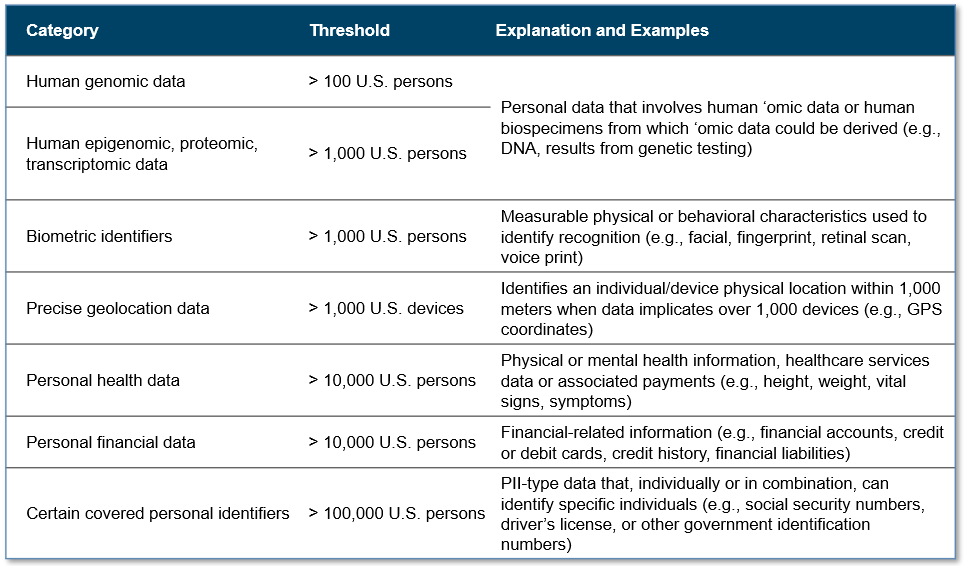
The Rule prohibits certain data brokerage and covered data transactions involving access to bulk ‘omic data or human biospecimens from which bulk ‘omic data can be derived. It also restricts vendor agreements, employment agreements and nonpassive investment agreements that would allow access to bulk sensitive data or government-related data. However, these restricted transactions may proceed if security requirements are satisfied.
The Rule specifies the countries of concern — China (including Hong Kong SAR and Macau SAR), Cuba, Iran, North Korea, Russia and Venezuela — and describes the covered persons with whom transacting could implicate the Rule if bulk sensitive data is involved.
The Rule also references specific guidance provided by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) related to the protection of bulk sensitive data.
- How Does the Rule Apply to Your Company?
There are two critical steps to comprehensively assessing whether the Rule applies to your company: (1) know your data and (2) know with whom you are transacting. Based on those steps, and setting aside exceptions or exemptions as may be provided by the Rule, below is a beginning framework for initially thinking about how the Rule might apply to your company:
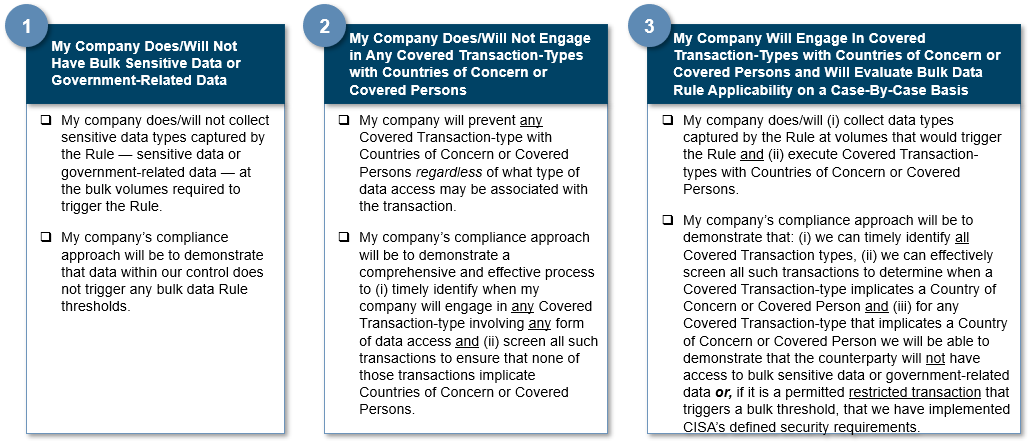
Successful compliance programs will be able to demonstrate consistency, accuracy and auditability with respect to their approach to compliance with the Rule:
- Consistency. Define in policy and employ a reasonable process to determine which use case applies to the company and periodically revalidate that the factors that informed the company’s initial assessment have not materially changed over time.
- Accuracy. Depending on which use case applies, develop and implement policy, process and technical controls that are sufficient to demonstrate compliance with the Rule.
- Auditability. Proving compliance with the Rule can be achieved by quickly marshaling documentation or information sufficient to demonstrate that the company’s compliance controls are effective.
At bottom, “reasonableness” likely will be the regulatory touchstone for determining the sufficiency of a company’s compliance approach. What is reasonable under the circumstances is a somewhat amorphous standard, however, and the criminal and civil penalties that can apply to any enforcement action under the Rule likely counsel companies to be conservative and protective.
- What Should Be Considered When Building a Responsive Compliance Program?
Companies already should begin thinking about how to develop and document a tailored covered data compliance program to mitigate operational and IT governance risk, including undertaking necessary due diligence, risk assessment and risk remediation efforts.
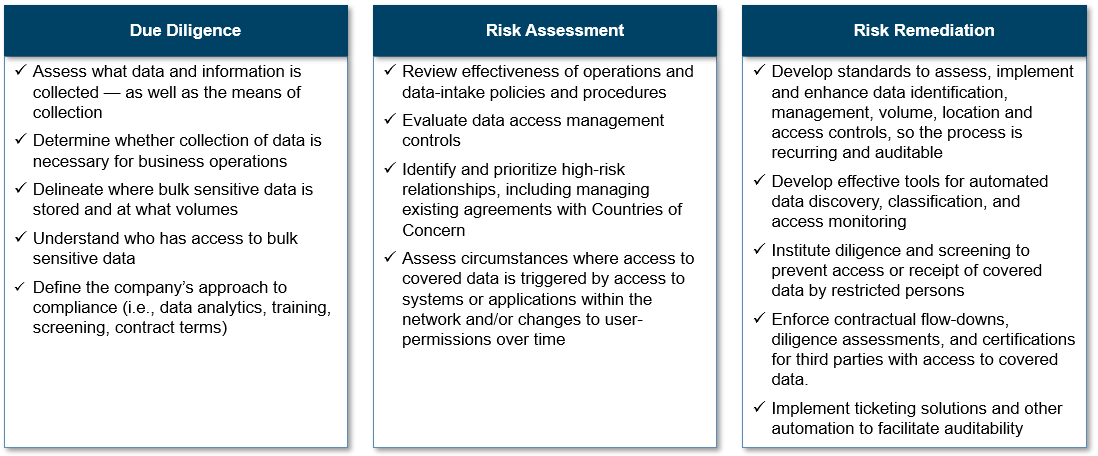
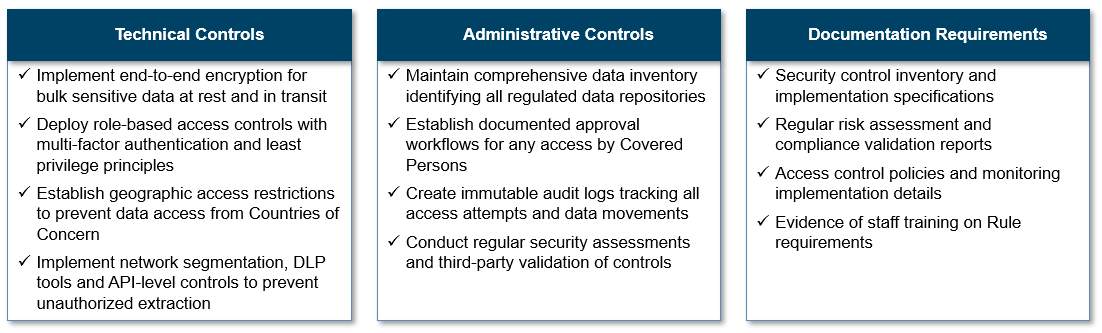
Companies also need to be considering the IT governance angle based on the incorporation of CISA guidance, including accounting for the following considerations:
- How Might the Rule Impact Multinational Organization and Cross-Border Transactions?
While impacts on specific market sectors and activities will be better understood after the Rule takes effect, with respect to multinational organizations and cross-border transactions, it should be expected that the Rule will create additional hurdles. Possible examples could include:
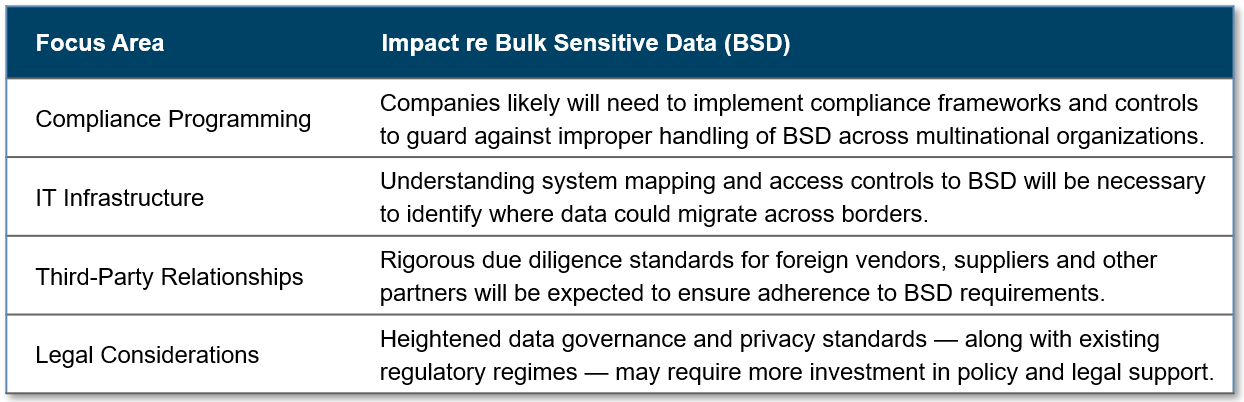
Multinational organizations and companies that engage in cross-border transactions should brace for these additional impacts and tailor their due diligence, risk assessment and mitigation efforts to reflect these additional considerations as deemed necessary.
- What Happens After April 8?
There are various complex variables surrounding the implementation of the Rule, but certain assumptions likely can be made. First, the Rule appears to be on a glidepath to effectuation. At this point it would require significant action within a limited temporal window to stop the Rule from taking effect. The Rule will be a requirement to which the market must be responsive. Second, the facts that the Rule is administered by DOJ (which is an agency focused on prosecution) and enforcement penalties for violations include, in certain instances, criminal liability, tend to indicate momentum behind aggressive Rule enforcement. Third, there likely will be some limited temporal period for the market to implement controls responsive to the Rule as DOJ staffs and begins engaging with the market on compliance. Fourth, DOJ staffing and capacity might be expected to increase over time given seeming alignment between the purpose of the Rule and broader political and strategic tailwinds for preventing exploitation of sensitive data by foreign persons and entities.
****
The bottom line is that companies need to be proactively assessing whether the Rule implicates their business, and if it does, come mid-April they need to be well on their way to developing a comprehensive controls approach scheduled to expediently achieve full implementation.
[1] Subject to the Federal Civil Penalties Inflation Act, civil penalties can be up to $368,136 or twice the amount of the transaction involved, whichever amount is greater. The Rule establishes the processes for DOJ to issue findings of violations and civil penalties, including an opportunity for parties to respond before the Department issues a penalty. Willful violations can lead to criminal fines up to one million dollars ($1,000,000) and up to 20 years' imprisonment.




